After seeing some suspicious activitiy in my McAfee antivirus logs, I learned the Access Protection functionality, specifically IRC communication setting may be able to thwart some of the aforementioned activity. There are a number of useful setting to log or even block attempts that are not enable by default. A test environment was setup using a IRC daemon on Remnux and a Nmap plug-in called irc-info.nse. An initial baseline scan/connect is made to confirm that the service residing in the virtual guest was working as advertised.
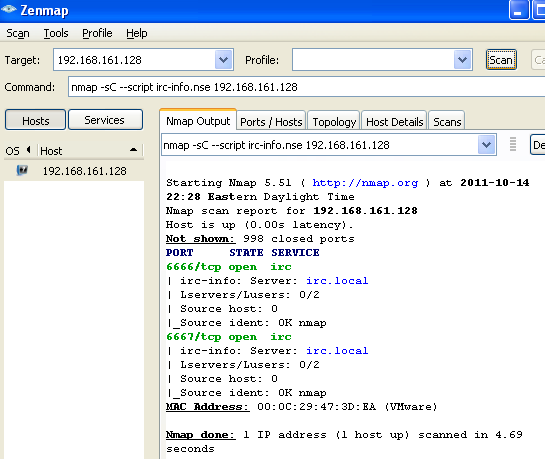
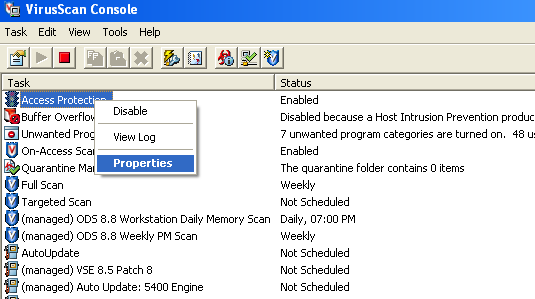
The host indeed had a IRC server running. We do not want our host communicating with IRC daemons so we can leverage McAfee to help us block the communication attempts. First, open up the Auto Protect settings in the VirusScan console.
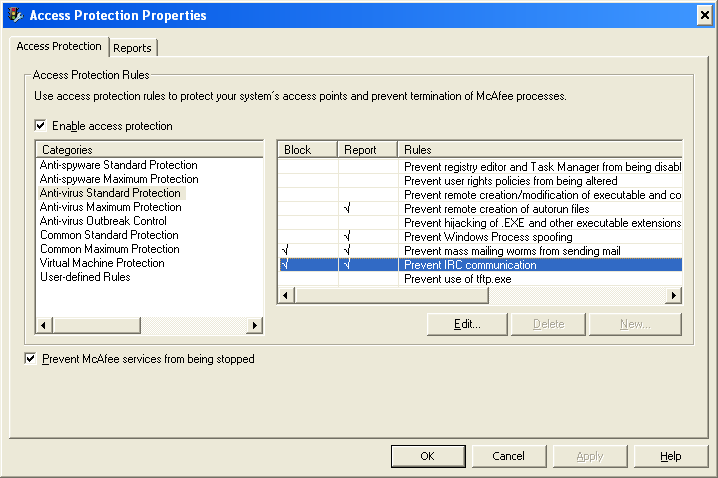
Next, “Prevent IRC communication” was enabled. This hosts processesshould not be making outgoing requests. If there were such requests from a process it could be indicative of malicious software contacting a C&C.
Now the policy is being enforced, we again test the ability to connect the remote hosts IRC service.
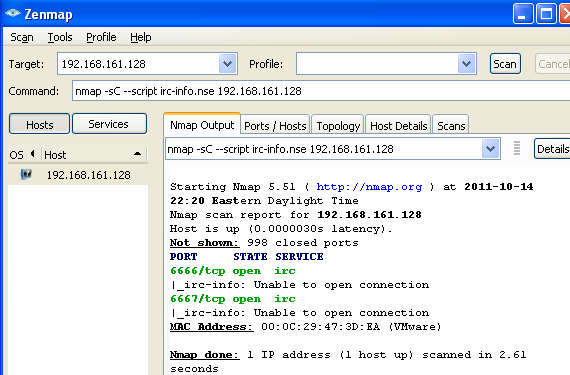
Nmap is able to elicit responses from the host but is unable to complete a connection to interact with the IRC server. The last screen shot depicts log entries reporting, and a blocking and reporting entry.

Be cautious of shunning all processes for a specific check as some applications may inadvertently use a port that a malicious process would typically use. Instead, consider white-listing those or one selecting known evil.
Comments
comments powered by Disqus